1Password has finally begun rolling out support for passkeys in its password manager. Passkeys are a login method that doesn’t require links or two-factor authentication codes. The feature has been available to 1Password users in beta since June. To use passkeys on a desktop computer, you’ll need to download the 1Password extension, which works with […]
CyberSecurity
Gadget Advisor presents a range of topics related to cybersecurity, including the latest threats and vulnerabilities, best practices for protecting against cyber attacks, and the latest tools and technologies for safeguarding against cybercrime.
Microsoft’s AI researchers accidentally leak terabytes of sensitive data
Microsoft’s AI researchers have inadvertently exposed dozens of terabytes of sensitive data, including things like private keys and passwords, when they published training data for open source on GitHub. GitHub users were instructed to download the models from an Azure Storage URL, but the security firm Wiz discovered that this URL provided access to the […]
How to set up proxy servers on your browser
Proxy servers are one of the best tools for ensuring privacy and anonymity online. With the help of two main types: datacenter and residential proxies, you can cover tons of use cases with both personal and commercial applications. For the average internet user, learning to use a proxy server may save you from paying for […]
It may be smart to update your browser now
Google, Mozilla, Microsoft, and Brave have all released critical security updates for their browsers. The updates address a vulnerability that an attacker could exploit to gain access to or execute malicious code on your computer, and the companies say that the vulnerability has been actively exploited in the wild. The vulnerability is related to the […]
Chrome gets a new way to track users
In conjunction with the new design of Chrome, Google has begun rolling out its new advertising technology called “Privacy Sandbox,” which tracks web pages and generates a list of advertising topics shared with web pages upon request. The platform has faced significant opposition but is still being released to the majority of Chrome users today. […]
Top 3 Trends in Security System Technology
Security system technology is quickly developing to meet the demands of a complex and connected world. New technology trends, however, are taking the world by surprise as their advancement redefines security measures. As cyber-attacks become more complex and advanced, attack defense techniques also get more sophisticated to keep up with the expanding difficulties. With traditional […]
Global botnet taken down
The U.S. Department of Justice states that the FBI, in collaboration with international law enforcement agencies, has successfully dismantled QakBot, a botnet that has been utilized by hacking groups for ransomware attacks and other cyber-related crimes for fifteen years. The botnet consisted of around 700,000 infected computers, with 200,000 of them located in the United […]
Microsoft makes some of its security tools free
Microsoft has announced that it will make certain security tools for their cloud services free, allowing their customers greater opportunities to analyze logs of activities within the services. Microsoft’s decision comes after hackers believed to be from China gained access to emails from U.S. agencies. The tools that Microsoft is now releasing for free were […]
Hackers enter the battle for Reddit’s API pricing
A hacker group calling themselves BlackCat, also known as ALPHV, claims responsibility for the February cyberattack on Reddit. The group now threatens to leak 80GB of data they allegedly obtained unless Reddit withdraws the price increase that third-party developers are now required to pay to use Reddit’s API. As we know, Reddit’s API price hike […]
Password Manager Chrome gets biometric support
The password manager in Google Chrome is quite handy to have and works perfectly fine if you don’t want to splurge on services like Bitwarden or 1Password. Soon, Google’s password manager will become even more convenient as it will receive biometric authentication support on Windows and Mac. This functionality has been available on mobile devices […]
Smart Homes for Kids: Best 27 Tools for Parental Control and Child Safety
As homes become smarter, the advantages are impossible to ignore. They provide an added layer of comfort, convenience, and, importantly, security for homeowners. Yet, the rise of this technology also prompts a significant concern: how can we ensure the safety and privacy of our children in such environments? The issue of child safety in smart […]
Android app recorded users every 15 minutes
The Android app iRecorder Screen Recorder, which started as an innocent screen recording app, reportedly began recording one minute of audio every 15 minutes and transmitting these recordings via an encrypted link to the developer’s server. The app was initially released in September 2021, but it was about a year later that it began recording […]
Google roll out support for passkeys
Google now supports passkeys, which are meant to be a more convenient and secure alternative to passwords. Passkeys work on all major platforms and browsers, allowing users to log in by unlocking their computer or mobile device with their fingerprint, face recognition, or a local PIN code. When creating a passkey on your Google account, […]
The new Google Authenticator is not end-to-end encrypted
The new feature that allows users to sync their one-time codes between multiple devices in Google’s two-factor authentication tool, Authenticator, does not use end-to-end encryption, which can expose users to significant security risks, according to security researchers who have examined the new feature. However, you can still use Google Authenticator without linking it to your […]
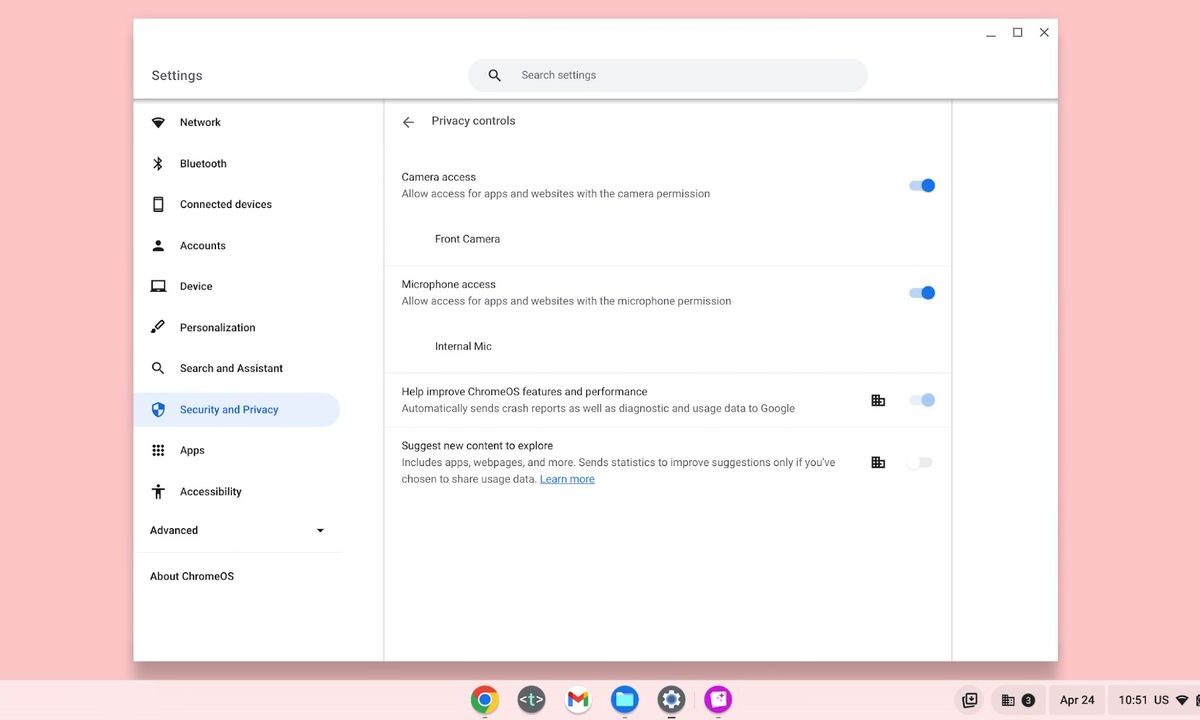
ChromeOS gets new privacy controls for camera and microphone
Google is adding new system-wide options for camera and microphone access in ChromeOS settings that can immediately block all apps and websites from being able to use them. The new privacy controls disable the rest of the computer’s access to the hardware. The software feature is meant to function like a physical on/off switch for […]
Google Authenticator can now synchronize with your Google account
Google is now updating its Authenticator app with support for synchronization of users’ one-time codes to their Google account on both iOS and Android. This means that you can still access your one-time codes if your phone, for example, is lost or stolen. Support for synchronization to your Google account should now be available to […]
Proton releases password manager
Proton, the company behind the security-focused email service Proton Mail, is now launching its own password manager. Proton’s password manager is called “Proton Pass” and stores login information for various services with end-to-end encryption (E2EE). In addition to usernames and passwords, it is also possible to store web addresses and email addresses for the services […]
Microsoft introduces Security Copilot
Microsoft has unveiled its new AI-based security service, Security Copilot, which may make it easier for companies to protect their computer networks from intrusions and attacks. Security Copilot is based on OpenAI’s language model GPT-4 in a similar way to how Microsoft has previously used OpenAI’s technology in its search engine Bing, Microsoft 365, and […]
Linus Tech Tips Youtube Channels Were Hacked
The past 24 hours have been very stressful for one of Youtube’s largest tech content creator. He had all three of his channels hacked in the middle of the night. Even though it was fixed within a few hours losing your primary income and not knowing that it will be fixed is VERY stressful. What […]
Google blocks apps from Chinese Pinduoduo
Yesterday, Google began flagging more apps from Chinese e-commerce giant Pinduoduo as malware in the Play Store. Users attempting to install, or who have already installed, apps from the company have reportedly received a warning on their device. Over the past few weeks, several Chinese security researchers have accused Pinduoduo, which is a growing e-commerce […]
Twitter discontinues two-factor authentication via SMS
If you have not switched from two-factor authentication via SMS on your Twitter account before today, March 20th, your account will have two-factor authentication deactivated. From now on, only accounts subscribed to Twitter Blue will have access to the security feature. It is still possible to use two-factor authentication via an authentication app without a […]
Google: Hackers can access your Samsung phone
Google’s security team, Project Zero, has discovered serious security flaws in Samsung modems that are installed in devices such as Pixel 6, Pixel 7, and Galaxy S22. According to a blog post, several Exynos modems have a vulnerability that could allow a hacker to remotely control a phone without any user interaction. The only thing […]
Revealing information on the LastPass Hack
LastPass had a tough year in 2022 due to several hacking incidents that exposed serious weaknesses in its security system. The attacks were carried out by threat actors who were able to steal LastPass’s source code and exploit a vulnerability in a remote-access app used by its employees. The hackers installed a keylogger onto the […]
These Android Keyboard Apps With Over 1 Million Installs Can Be Hacked Remotely
Android keyboard apps are a popular way for users to customize their phone’s typing experience. However, a recent report has found that some popular keyboard apps with over 1 million installs can be hacked remotely. This means that a cyber attacker could potentially gain access to sensitive information, such as passwords and financial data, through […]
What Is Account Takeover and How to Prevent It?
Malicious people use account takeovers to change your online identity, access all of your information, delete you out of various accounts, spread viruses, and stalk you. This is highly prevalent in today’s world, where social networks are becoming more popular. For example, websites like Facebook and Twitter provide new opportunities for stalkers to follow you […]
3 Home Security Tips and Guidelines You Never Thought Of
There are plenty of security devices and gadgets that are quite well known and widely employed. We just keep coming up with new ways to defeat those burglars. Clearly, staying on top of these things is necessary, so the more, the merrier. For many, there’s a lot to bear in mind with all this equipment. […]
No One is Safe from the Data Breach Epidemic
Hacking cases have grown a lot in recent years, haven’t they? Every other day there is news of some large corporation’s data being illegally accessed and exposed, an individual’s bank credentials being used by unauthorised hands, or government records getting published by an elite hacking group. These are examples of data breaches. The threat is […]
Survey Reveals the State of Cybersecurity Training
The industry-leading penetration testing and vulnerability management firm surveyed over 1200 employees and asked them many questions regarding their cybersecurity habits and know-how. The results were shocking. 69% of the employees have received cybersecurity training, and yet, when asked to take a basic cybersecurity quiz, 61% failed. 17% of those working in the field of […]
Proven Practices to Secure a Your Internet Connection That Won’t Fail
Not only has Internet security become a major problem nowadays, but it also represents one of the top priorities of an average Internet user. Using software such as a password manager can surely contribute to spending a more relaxed time while surfing. However, there are some other proven practices to secure your internet connection that […]
Four Tips on How to be more Private online
The world has become a global village and the current internet age comes with its dangers. There are more cases of identity theft and hacking than ever and this has made online security very important for internet users. Here are four tips on how to attain anonymity when online. Conceal your IP address and Location […]