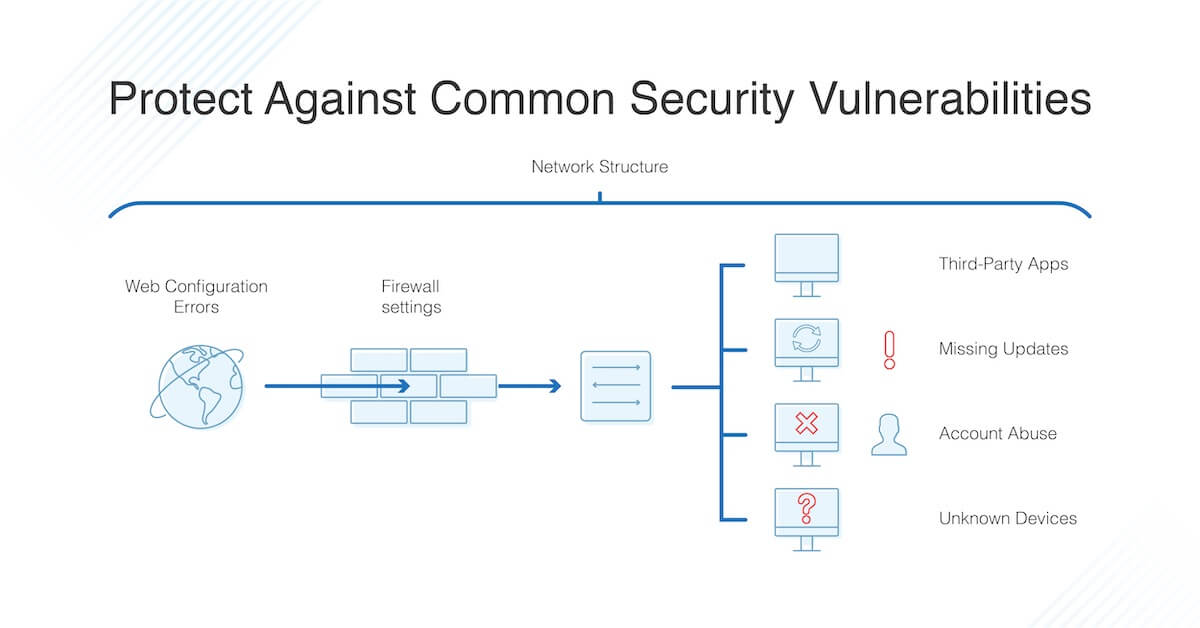
Think of a network like the wild-west. A vast open landscape that good guys and bad guys gallop through on the daily. Keeping the bad guys out of your virtual western saloon is often about as easy as winning a real-life gun duel. Fortunately, in our digital world, bad guys and threat actors can be stopped from ever trespassing onto our networks with a suitable network scan. Networks are wrought with vulnerabilities. If there weren’t any vulnerabilities, there would be nothing to exploit, but sadly that’s not the case. Software vulnerabilities exist because software applications are developed by humans. Humans make mistakes. Mistakes are easy for attackers and threat actors to exploit. This is where a good network scan can ride in to save the day.
Use Scanning Software Frequently
Utilize IP scanning software and network scans frequently to prevent attackers. All a true attacker needs are one vulnerability to use as a foothold into the entire network. At a minimum, every business should be scanning their network at least once a month. IP addresses should be identified and patches or remediation can be applied to vulnerabilities. Scanning your network quarterly as compliance requirements demand is not enough. After all, you can’t defend your network until you have conducted a security network scan and identified all of the critical assets. You can even automate your scan tools to scan devices and apps at certain times, but only scan after you’ve identified all vulnerabilities to show progress.
What should a network scan include?
Preventing threat actors means implementing a thorough scan. Every network scan should include all devices with an IP address (laptops, printers, and workstations, routers, hubs, and switches…etc.) as well as any software running on those devices. Unauthenticated scans can unveil vulnerabilities found in things running on your systems as well as open ports on devices that could potentially allow for malicious apps to run or communicate. However, it is always best to stick with authenticated scans to reveal vulnerabilities in applications such as Flash or Adobe Reader.
Who should run a network scan?
Can anyone in the office run a network scan or use IP scanning software? Technically yes, but the person running the scan should have a background in network and understand the breadth of vulnerabilities that exist and how they can be exploited. The person running the network scan should also understand every major feature of the scanning tool and which types of devices on the network are deemed most vulnerable. The process can be quite involved and time-consuming. Setting up scan configurations might only take about 15 minutes, but the scan itself can take hours or even days depending on the size of the network and the number of ports. Because of this most professionals choose to run the scan overnight as to not disrupt workers on the network.
The Takeaway
Network scans are absolutely paramount in policing the wild west that is a computer network. Not only can they help to prevent threat actors from exploiting vulnerabilities on the network, but they can help to keep information and data safe while maintaining network efficiency for increased productivity.